Why HITRUST compliance?
There’s no denying that healthcare organizations house numerous sensitive and crucial data. Records of patients and electronic health records (EHR) are essential and among the most highly valued assets on the black market. Shockingly, cyberattacks on healthcare facilities have exposed 385 million patients’ data within the past decade. This means cybercriminals have set their sights on healthcare organizations and targeting their cybersecurity measures.
Adhering to HIPAA regulations is necessary for the safety of EHRs. However, the path to HIPAA compliance can be intricate, time-consuming, and costly. This is where HITRUST comes into play. HITRUST established guidelines that simplify the process of complying with HIPAA regulations and equip organizations’ cybersecurity measures to withstand potential threats.
This article will examine the bigger picture of HITRUST compliance, including the requirements and importance of staying compliant. By the end, you will understand what it takes to secure HITRUST certification and how HITRUST compliance can benefit your organization in minimizing risks, optimizing compliance, and maintaining exceptional data security standards.
What is HITRUST?

The Health Information Trust Alliance (HITRUST is a non-profit organization dedicated to providing data security standards and certification programs that assist businesses in protecting sensitive data, confronting information threats, and achieving compliance objectives.
Established to offer the healthcare industry an alternative for handling information risk management through a network of third-party assurance evaluations, HITRUST aims to condense, decrease, and, in certain situations, remove the necessity for numerous reports. This design element is called “assess once, report many.”
What sets HITRUST apart from other compliance frameworks is its ability to consolidate information from a wide range of authoritative sources, including HIPAA, SOC 2, NIST, and ISO 27001. Moreover, it is the sole standards development organization equipped with a framework, assessment platform, and independent assurance program, contributing to its widespread adoption.
What is HITRUST Certification?

HITRUST developed the HITRUST Common Security Framework (CSF) as a systematic, measurable method for managing security risks when handling healthcare data and other sensitive information. Obtaining HITRUST CSF certification allows companies to show that the systems within their infrastructure adhere to the framework’s stringent standards and regulations. HITRUST-certified assessors conduct certifications and generate comprehensive reports to aid organizations in managing and enhancing their maturity levels.
The CSF contains 14 control categories comprising 49 control objectives and 156 security and privacy-related control specifications. Control objectives represent the desired outcome, while specifications dictate the particular tasks infosec teams must execute to meet the goals. These specifications can be in the form of policies, procedures, guidelines, practices, or organizational structures and may be administrative, technical, managerial, or legal.
The most recent version of the CSF (v9.6.0) consolidates 44 key security and privacy-related standards, regulations, and frameworks as authoritative sources. It employs a risk-based approach to assist organizations in tackling security hurdles through prescriptive and scalable security and privacy controls.
HITRUST vs. HIPAA: What’s the Difference?
Although HITRUST and HIPAA might seem similar at first glance, comparing them side by side would be misleading, as they serve different purposes and focus on different aspects of healthcare compliance and security.
While HIPAA is a law published by the government and policymakers, HITRUST is a framework established by security industry specialists that includes aspects of HIPAA.
The HITRUST CSF offers organizations an approach to demonstrate compliance with security controls mandated by HIPAA. HITRUST enhances the stipulations of HIPAA by integrating them into a framework focused on security and risk management.
It’s important to note that HITRUST doesn’t serve as a substitute for HIPAA compliance or a confirmation that an organization is HIPAA compliant. However, it is broadly accepted and considered the gold standard for information protection assurance.
Why HITRUST Compliance Really Matters

HITRUST has gained significant recognition in the healthcare sector as the go-to certification ensuring compliance with HIPAA. Thanks to its widespread adoption within the current context of the healthcare data explosion, HITRUST offers a unified approach to address third-party risk from business associates.
Adopting the HITRUST CSF delivers numerous tangible and intangible advantages. As you delve into the world of HITRUST, consider these important points:
- HITRUST is the most widely adopted security framework in the U.S. healthcare sector. The framework encompasses all HIPAA and HITECH requirements, ensuring coverage of healthcare-specific security, privacy, and regulatory concerns. As such, 83 percent of hospitals and healthcare providers have adopted HITRUST.
- HITRUST compliance enhances risk management. The HITRUST CSF is invaluable for all organizations in compliance-driven industries, as it guarantees robust, well-documented, and consistent risk management practices. Any organization aiming to safeguard patient or customer data, intellectual property, and other sensitive data can benefit from adhering to its guidelines. HITRUST is also slowly becoming a standard in the heavily regulated finance industry.
- HITRUST is required by many of the leading payers. In 2016, a group of five major healthcare payers sent a letter to their business associates, emphasizing the importance of obtaining HITRUST certification within a two-year timeframe. Fast forward to today, over 90 healthcare payers mandate that their third-party service providers achieve HITRUST certification.
- HITRUST framework is continuously updated to handle modern regulations and cybersecurity threats. Regular revisions and expansions are made within HITRUST framework to ensure healthcare organizations remain prepared for any new security risks that may arise. This ongoing review and improvement process guarantees a constantly updated security posture, forging HITRUST-compliant organizations to update their defenses regularly against emerging threats and cyberattacks. As the most consistently updated security framework in existence, HITRUST requires quarterly updates and yearly audit changes, making organizations, who adhere to the CSF, maintain the highest security levels.
- HITRUST compliance shows a strong commitment to data security. Achieving HITRUST compliance demonstrates an organization’s commitment to data security and privacy. More specifically, this certification indicates that third-party auditors have conducted an in-depth analysis of the company’s IT and business environment to confirm that the highest security standards are in place. This can enhance trust among clients and stakeholders, leading to higher credibility in the healthcare market.
How to Get HITRUST Certification
HITRUST certification entails an extensive and thorough examination of a company’s security measures and risk management practices. To achieve this certification, organizations must adhere to a set of requirements called the Common Security Framework (CSF), which covers numerous areas, including access control, risk management, network security, and incident handling.
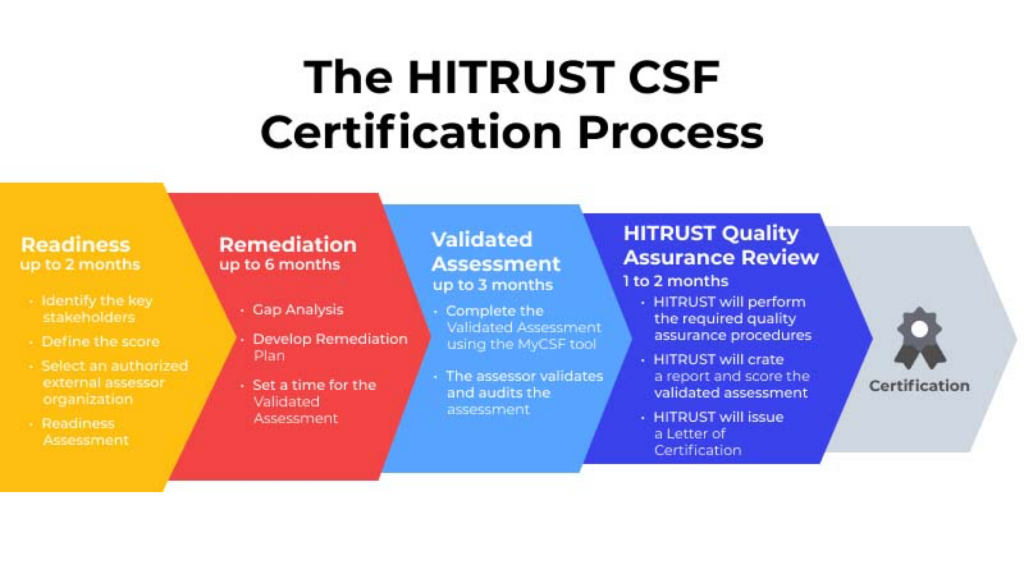
To successfully achieve HITRUST certification, organizations must complete the following stages:
1. Readiness Assessment and Gap Analysis
Determining the scope is the key first step, as it defines which business units and subsidiaries are involved, as well as what is covered by controls. At this stage, the scope should be determined as detailed as possible so that you can define all the requirements needed for achieving the HITRUST certification.
Many organizations turn to a certified HITRUST expert assessor to support them in defining the scope, choosing the assessment type, and establishing the necessary controls. Careful scoping allows your organization to optimize time and resources while gearing up for the HITRUST evaluation process.
Once the scope is determined, the HITRUST assessor will examine all the documentation, policies, and procedures against HITRUST requirements. Testing is conducted to ensure that controls are functioning correctly and any gaps identified are documented for remediation.
The duration of this process can vary, taking up to 8 weeks depending on the company’s infrastructure complexity.
2. Gap Remediation
During the readiness phase, your organization need to address any performance or documentation gaps identified. The main objective of this phase is to assess and prioritize gaps in your company based on the risk levels. This allows you to proactively address and resolve any issues before proceeding to the validated assessment.
In the remediation phase, authorized assessors will focus on understanding the your environment and the normal data flow through its systems within the defined scope. They will analyze requirements to gain insight into the your controls, identify gaps, and propose feasible solutions. As the company works towards resolving these issues, assessors will provide ongoing support and monitor progress towards achieving compliance.
Depending on the type of required remedial actions, this process can take up to 6 months during the first year.
3. HITRUST Compliance Validated Assessment
Throughout the verified evaluation process, expert evaluators carry out tests on specified control requirements for each assigned category. A standard on-site risk analysis typically involves interviewing key staff members, examining relevant documentation, performing samples, executing penetration tests, and conducting vulnerability assessments. Every requirement is then assessed and scored based on the following attributes detailed in the control maturity framework:
- Policy – 15%
- Procedure – 20%
- Implemented – 40%
- Measured – 10%
- Managed – 15%
According to these control maturity levels, the compliance levels are as follows:
- Fully compliant
- Mostly compliant
- Partially compliant
- Somewhat compliant
- Non-compliant
During this stage, assigned assessors must thoroughly assess and confirm the organization’s ratings. Subsequently, the finalized assessment is forwarded to HITRUST for approval. The ultimate decision to approve or reject the certification application lies with HITRUST.
4. HITRUST’s Quality Assurance Review and Certification Maintenance
Once the validated assessment has been finalized, it will be sent to HITRUST for quality assurance checks and to generate the finalized report. The standard processing time for submission by HITRUST falls between 4 to 8 weeks.
After this time, HITRUST will grant you the certification if your performance is satisfactory. However, if it falls short, you will receive a letter outlining the reasons for the failed evaluation and a corrective action plan to help you attain the certification.
Please note that achieving HITRUST certification is not a one-time accomplishment. Your company must consistently adhere to the certification’s requirements and framework to retain its certified status. To maintain the HITRUST certification, a re-evaluation will be necessary every two years, typically involving less extensive assessments. Remember, ongoing compliance is vital for sustaining this certification.
KMS Healthcare Paving the Way to HITRUST Compliance
This comprehensive guide clearly demonstrates that achieving HITRUST compliance is a substantial endeavor, necessitating a significant investment of time, money, and effort. The certification process is rigorous, but the rewards are well worth the exertion. The advantages of heightened data security, mitigated risks, and an efficient, streamlined compliance process spanning multiple regulations and frameworks can more than offset the associated costs.
KMS Healthcare is your trusted development partner for maintaining top security standards throughout software product development. With our team of experts, we help organizations maintain the standards needed to achieve HITRUST certification and possess extensive knowledge and expertise in the healthcare industry. Our seamless approach ensures industry compliance and more.

Schedule a free consultation today to learn how KMS Healthcare can support you in attaining HITRUST compliance and beyond.

